Microsoft Entra ID (SSO)
Configuring Single Sign-On (SSO) with Microsoft Entra ID as an identity provider (IDP) for vScope allows enhanced security features, such as Multi-factor Authentication (MFA). By using Microsoft Entra ID to handle authentication and permission settings for vScope users, you can centralize access control and user management. This guide outlines the configuration steps.
Requirements
- Ensure you have permissions in Microsoft Entra ID to manage App Registrations.
- Confirm that vScope is installed in your data center and has remote access to Azure.
- Make sure an HTTPS certificate has been uploaded and saved in vScope.
- Ensure that the accounts have an registered email (same as user principal name) in Microsoft Entra ID, otherwise they will not be allowed to login using SSO.
- Currently, only Single-tenant SSO is supported.
Authentication
Creating an App Registration in Microsoft Entra ID
First, create an App Registration and configure permissions to allow vScope to read user and group data from Microsoft Entra ID.
-
Log in to Microsoft Entra ID at https://portal.azure.com/.
-
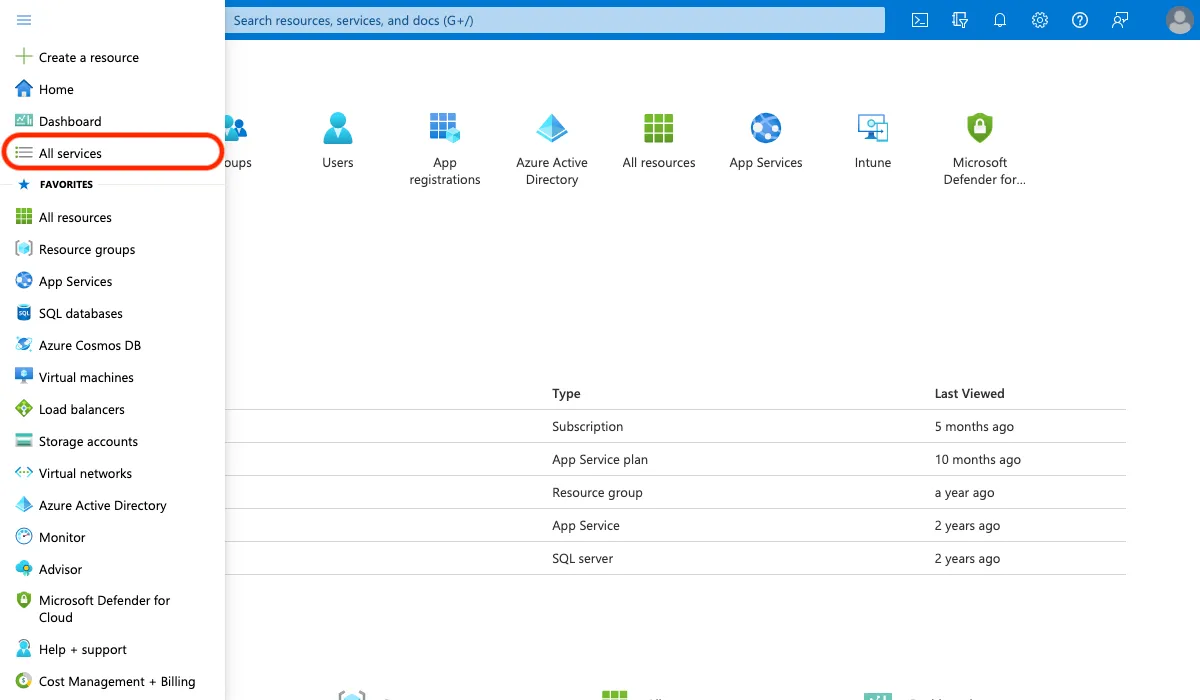
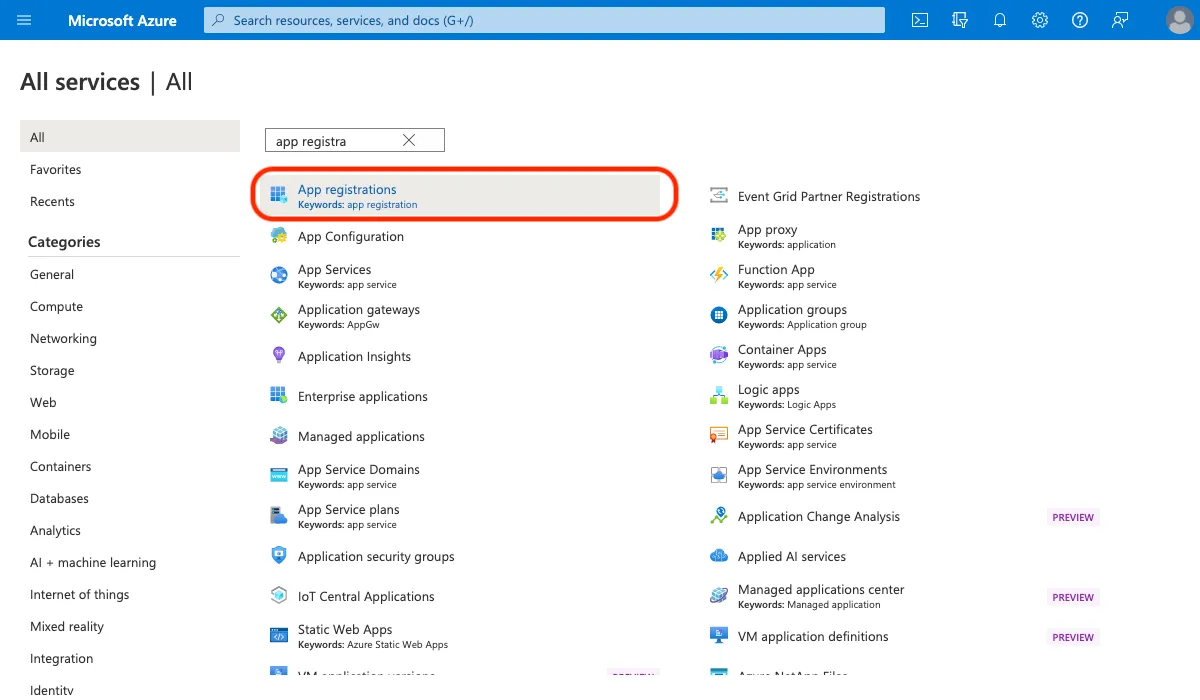
In the sidebar, locate All services, then search for and select App registrations.
-
Click + New registration to create a new App Registration.
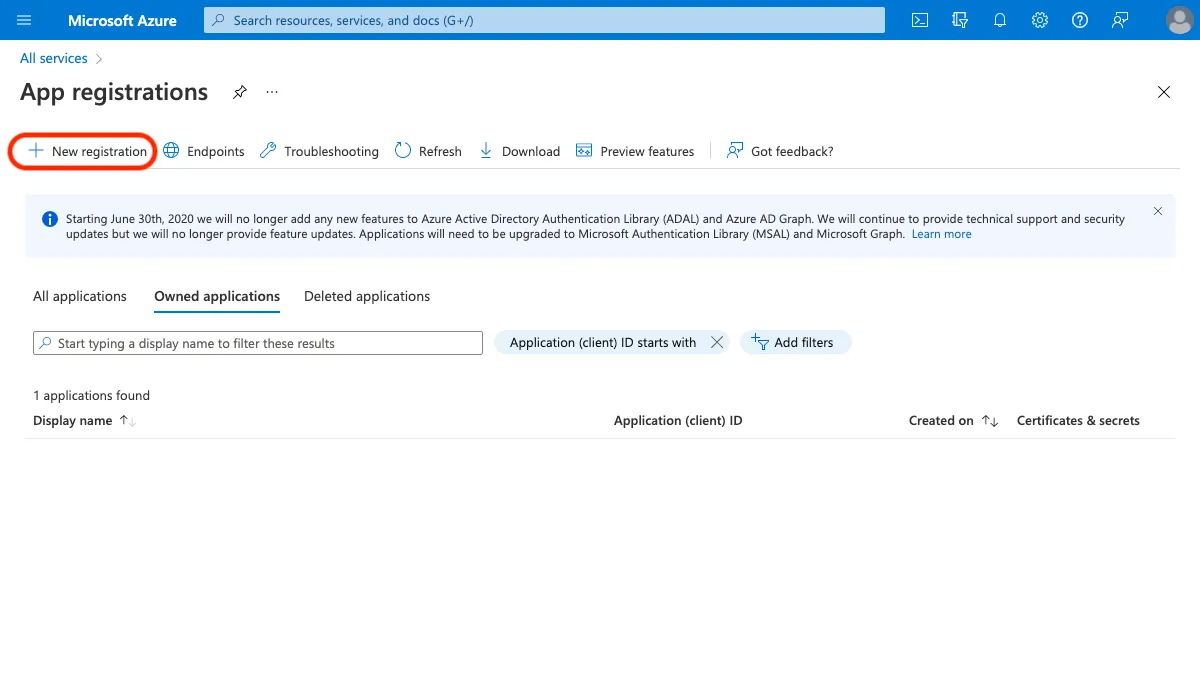
- Enter a name, such as vScope SSO.
- Under Supported account types, select Accounts in this organizational directory only (Single tenant).
- Leave Redirect URI (optional) empty and click Register.
Generating an API Key for the App Registration
This API key allows vScope to securely connect with Microsoft Entra ID.
-
In your app registration, navigate to Certificates & secrets.
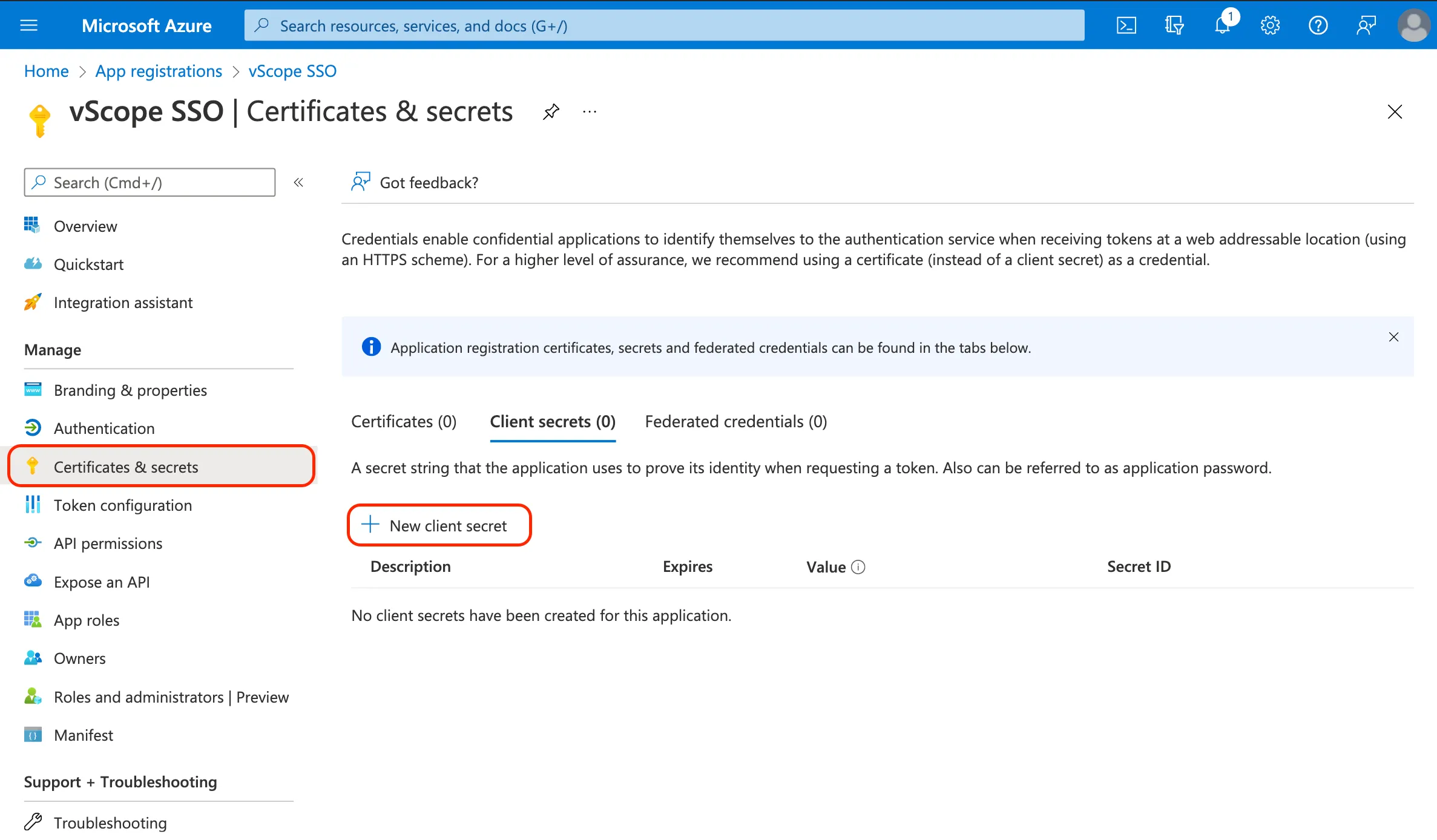
-
Click + New client secret and provide a description (e.g., “Used for vScope SSO”).
-
Set an expiration for the API key. Once it expires, you will need to generate a new key.
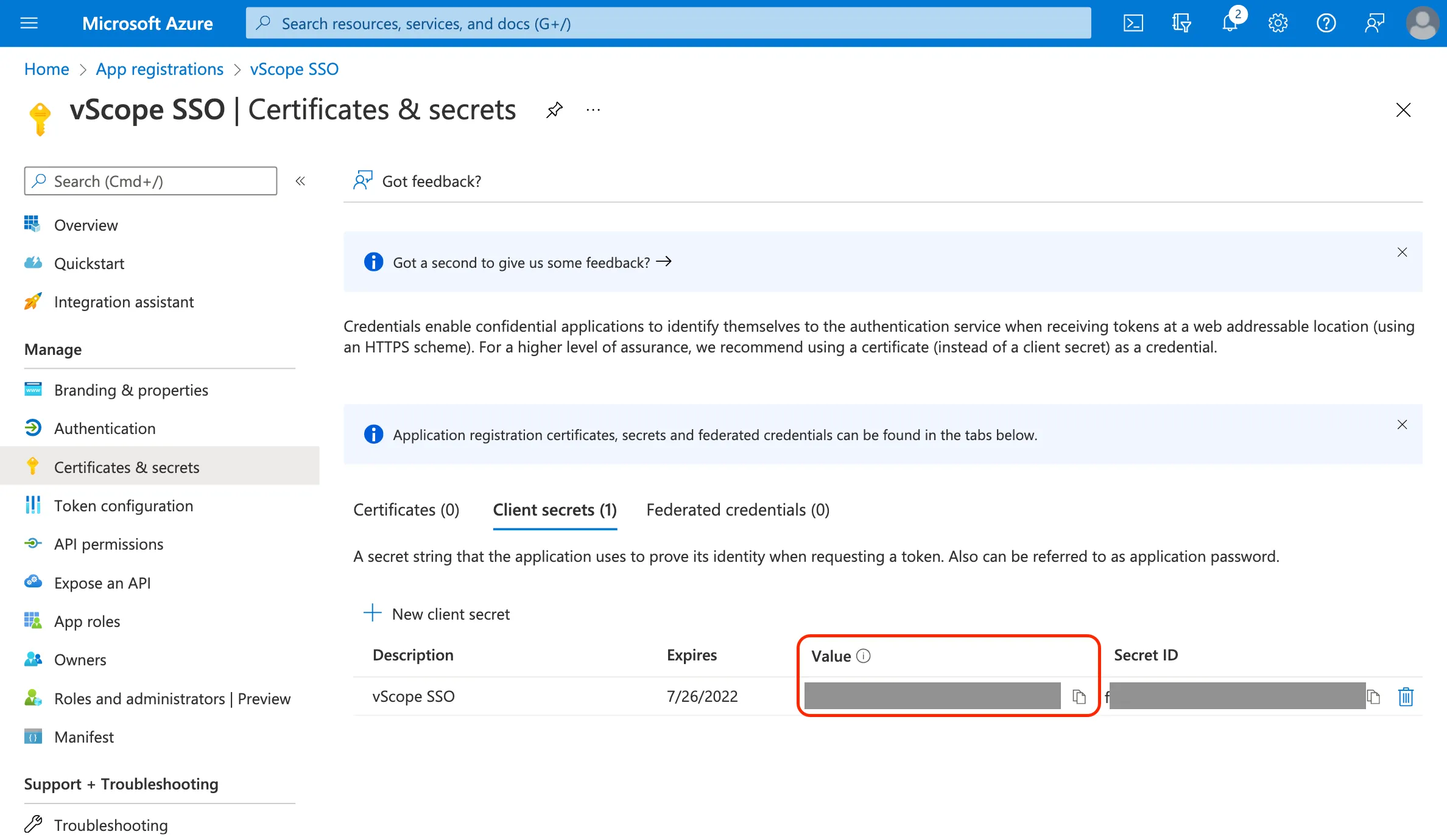
Important: Immediately copy and save the Value. This client secret is only visible upon creation.
Granting Permissions to the App Registration
Grant the necessary permissions for the app registration to read data from Microsoft Entra ID.
-
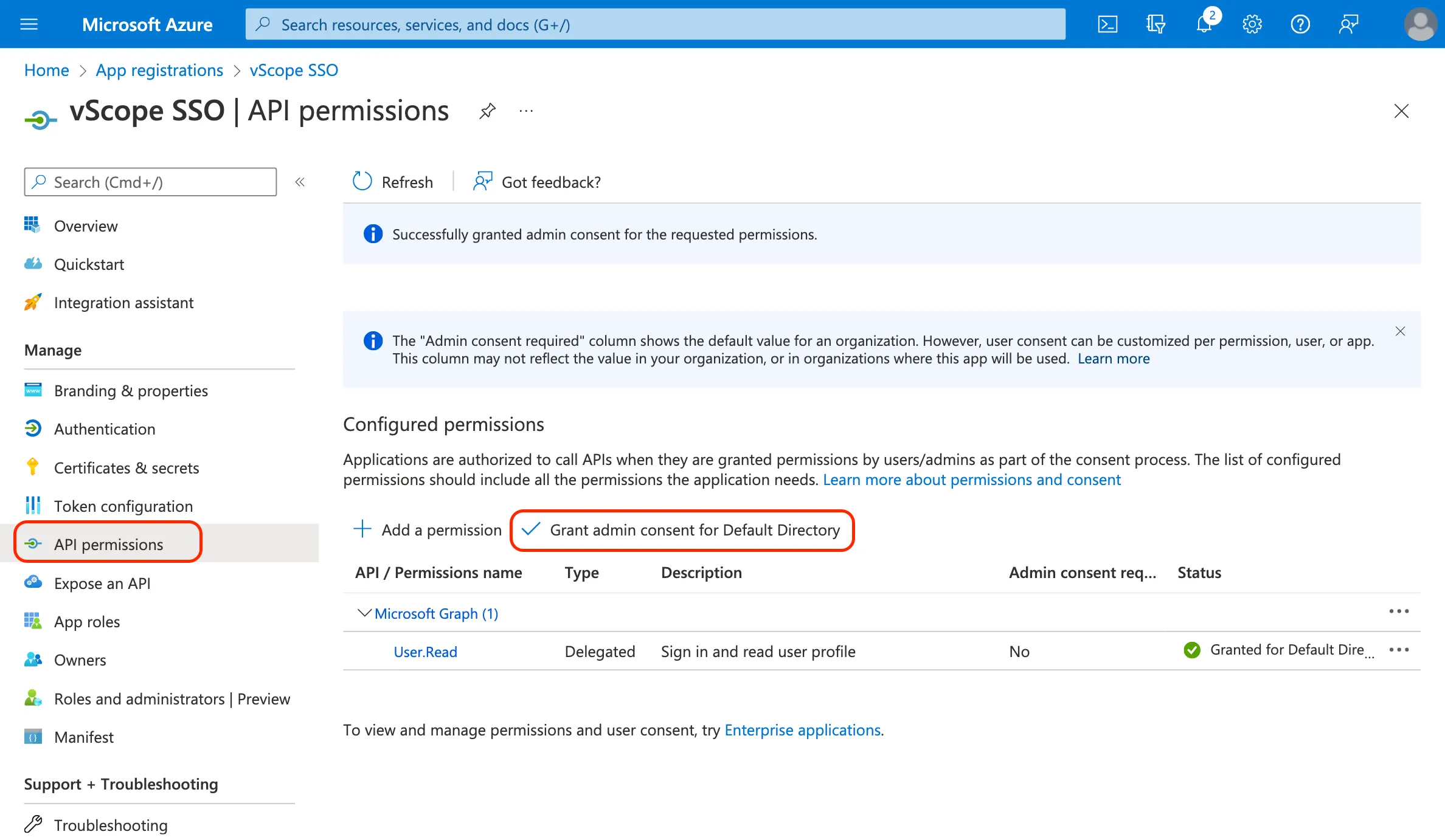
In the app registration, go to API permissions.
-
Click Grant admin consent for Default Directory to apply the permissions.
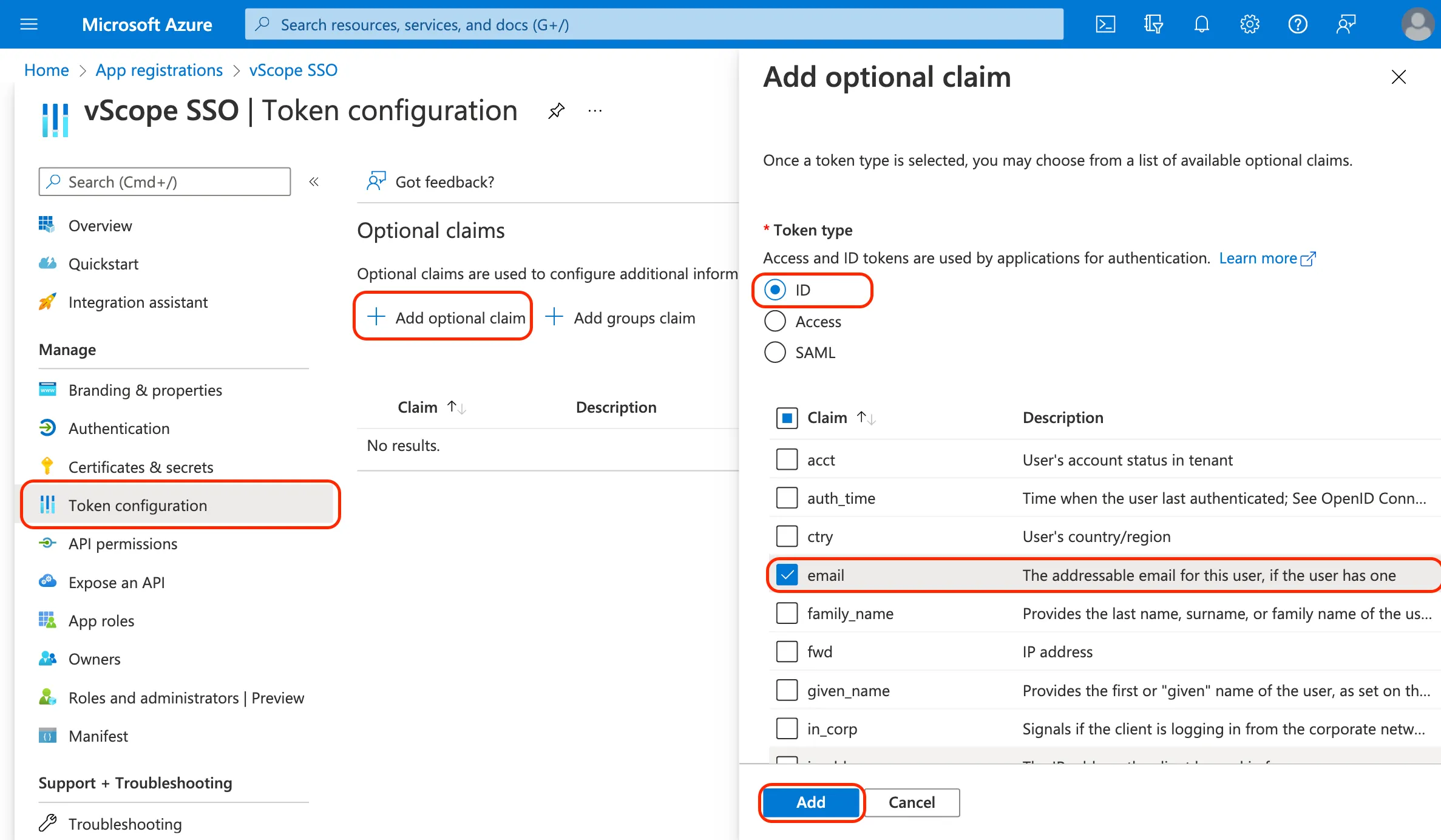
To allow vScope to use email as an identifier, grant permission to read the email property from Microsoft Graph API.
-
Go to Token Configuration > Add Optional Claim.
-
Set Token type to ID, select email as the claim, and add it.
Configuring SSO in vScope
In this step, enter the values from Microsoft Entra ID into vScope to complete the SSO configuration.
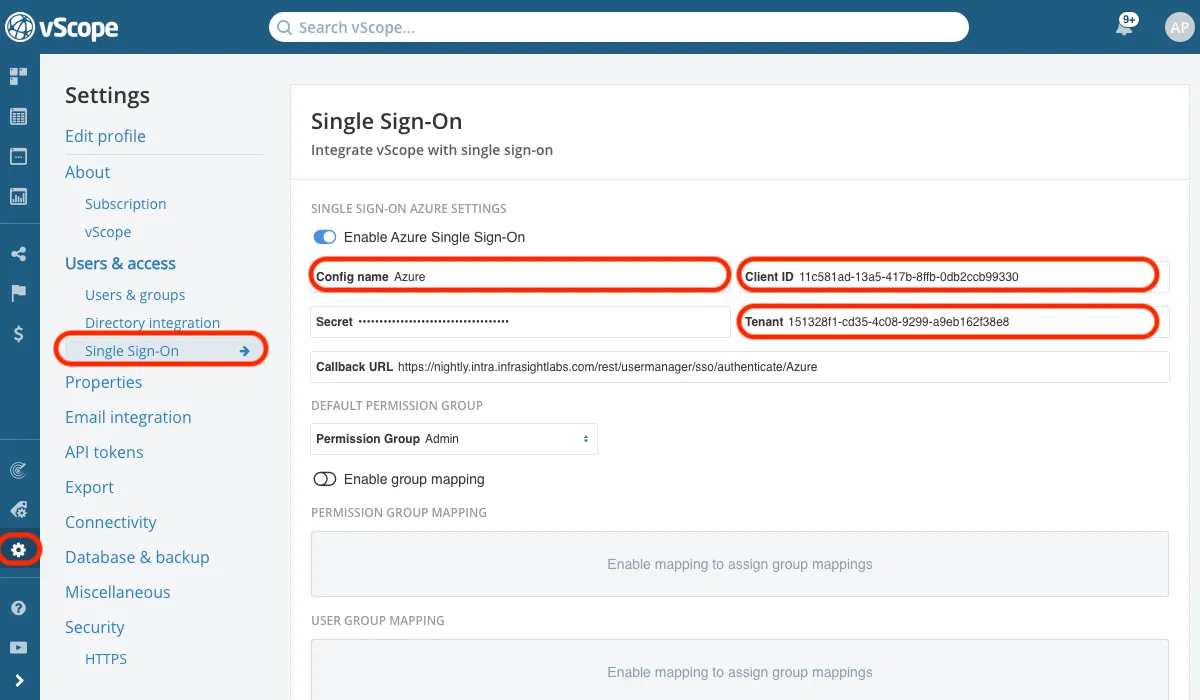
- In vScope, navigate to Settings > Users & Access > Single Sign-On and enable Microsoft Entra ID Single Sign-On.
- Set a configuration name, such as AzureSSO. (Use only letters and digits; this name will be used in the callback URL.)
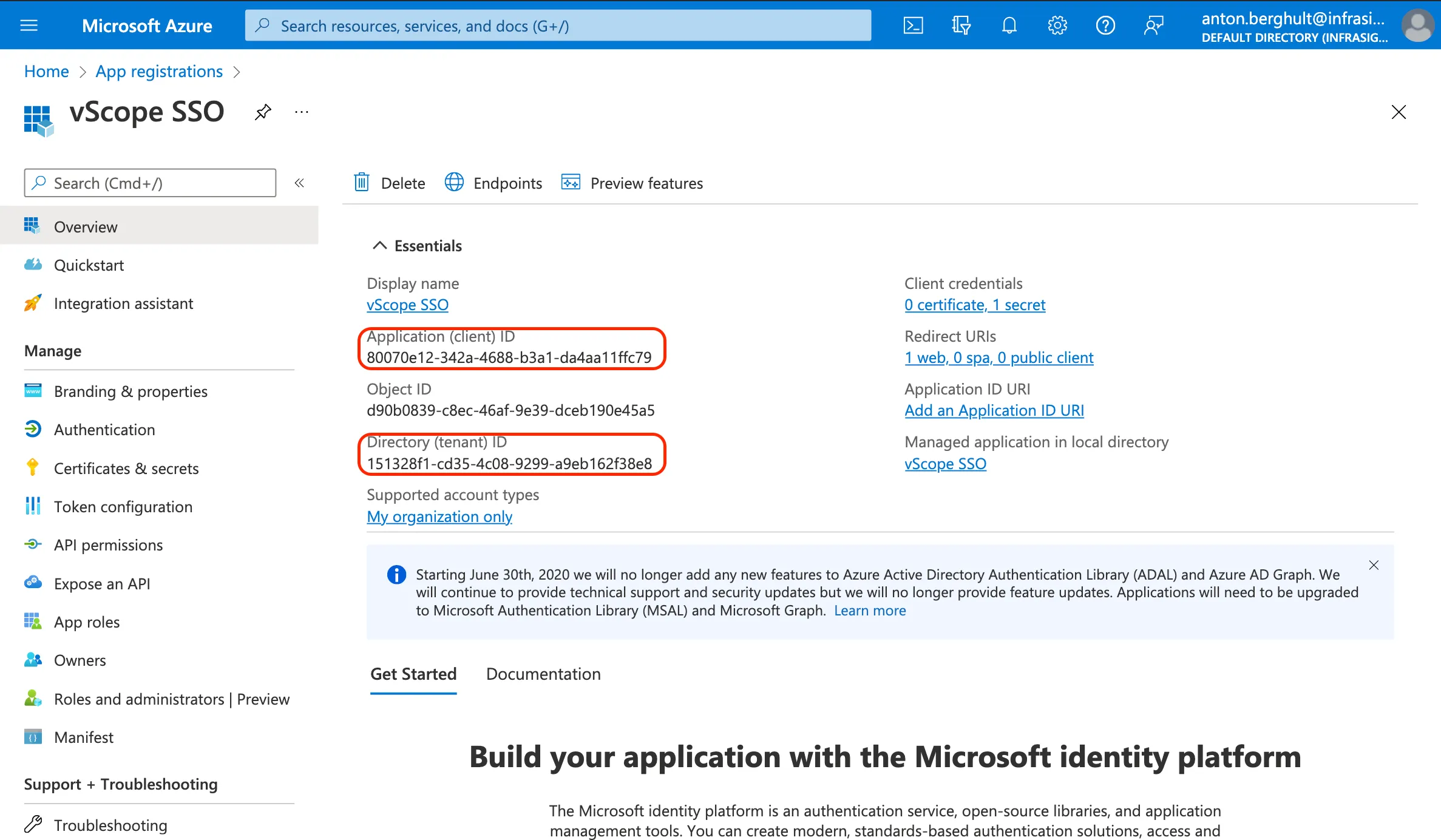
- Paste the ClientID (from the Application (client) ID).
- Paste the TenantID (from the Directory (tenant) ID).
- Paste the Secret (from the client secret Value).
- Save the settings to generate a Callback URL for the final step in Microsoft Entra ID.
Configuring Authentication for the App Registration
This step configures the callback URL in Microsoft Entra ID to enable authentication.
-
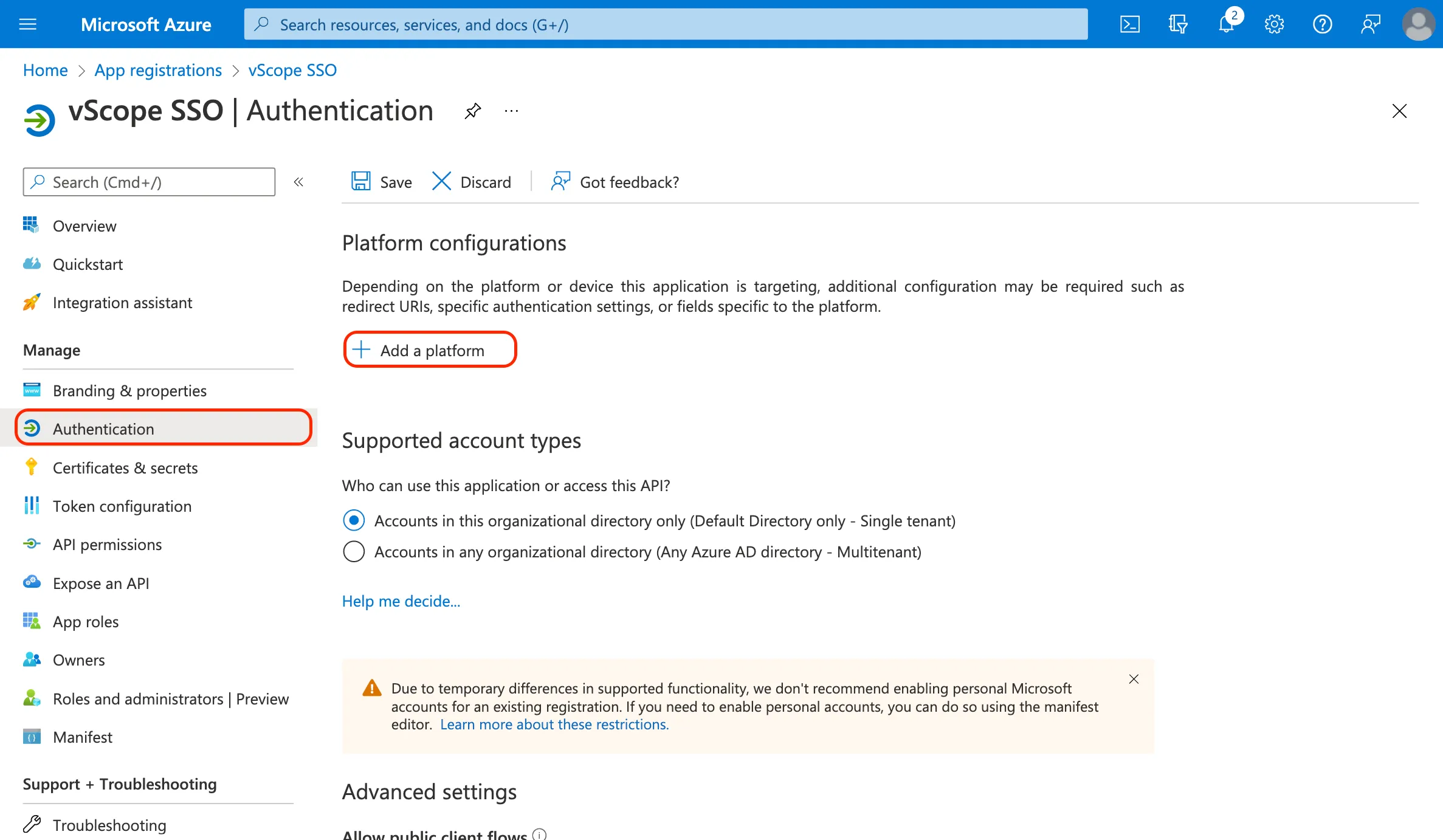
In the app registration, go to Authentication.
-
Add a new platform configuration by clicking + Add a platform and selecting Web.
-
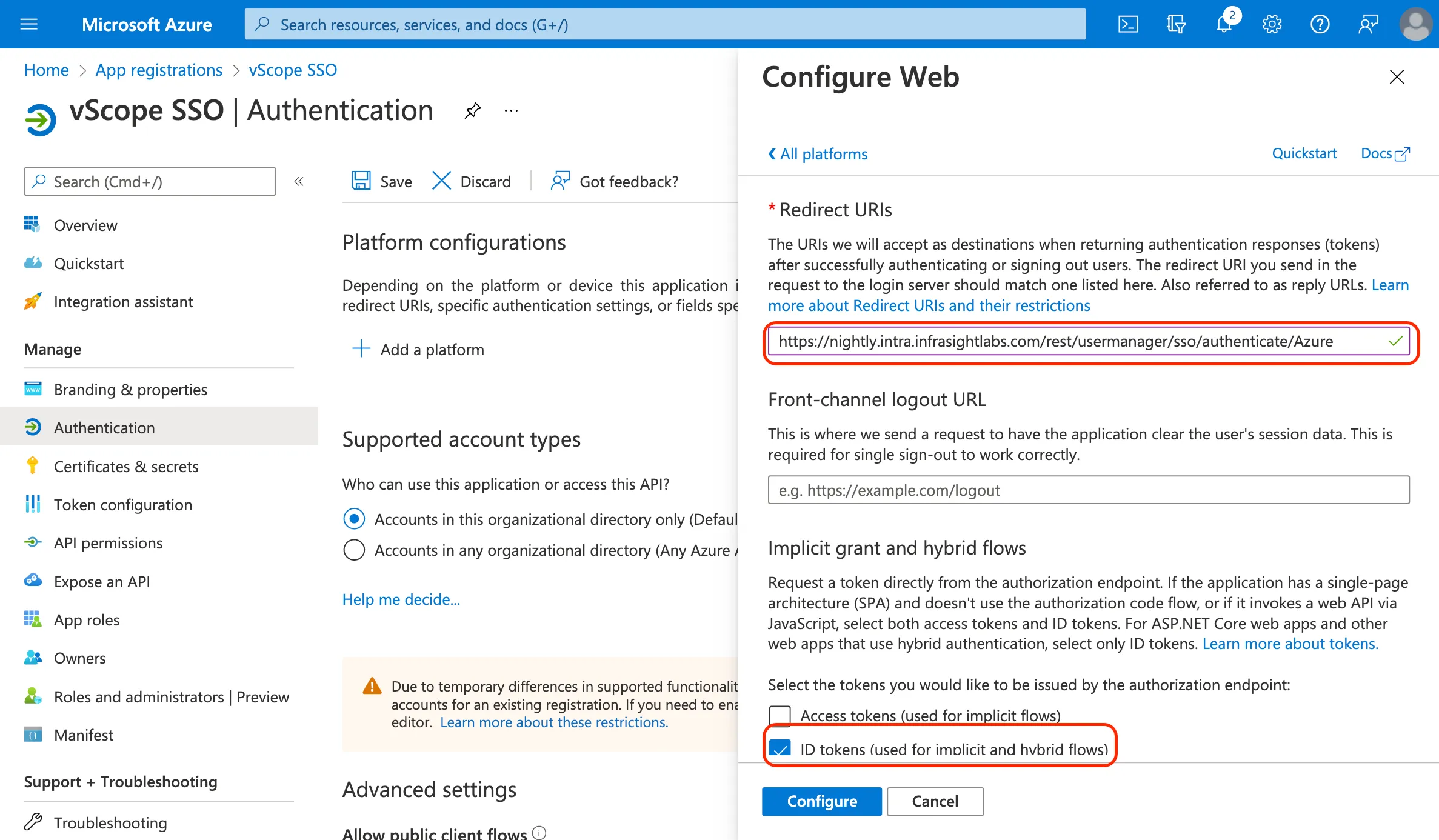
Paste the Callback URL from vScope into Redirect URIs.
Skip Front-channel logout URL. Enable ID tokens and click Configure.
Upon completion, vScope is now configured to use Microsoft Entra ID for SSO.
Group & Permission Mapping
To use Microsoft Entra ID for managing groups and permissions in vScope, configure group settings.
- In the app registration, go to Token Configuration and + Add groups claim.
- Choose settings for group mapping, such as adding users to groups based on Directory roles.
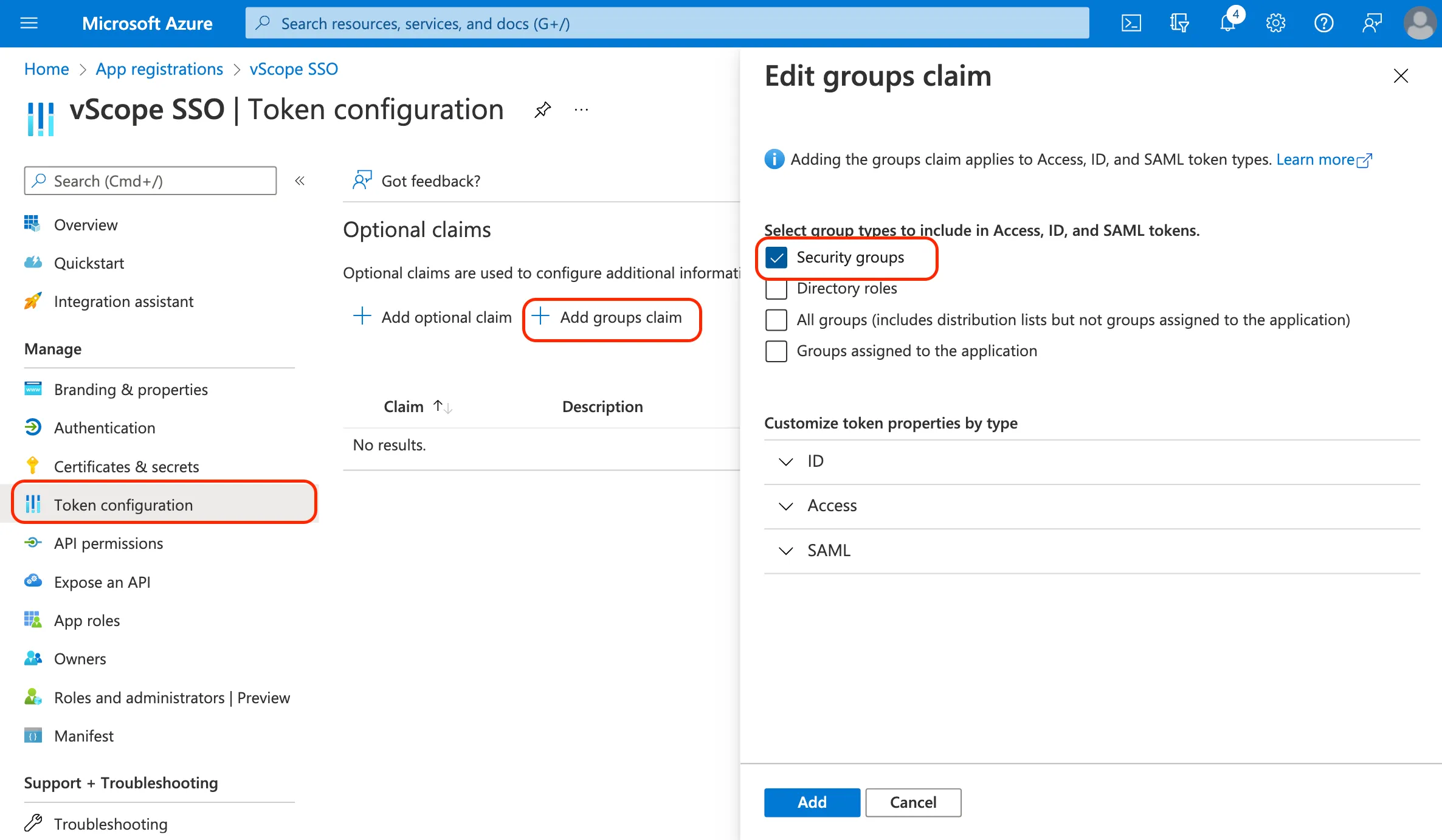
Learn more about group claims on Microsoft Docs.
Back to vScope…
- In Settings > SSO select Enable Group mapping
- Select Property in Azure: Choose the Azure property (e.g., group ID) to base your mapping on.
- Name the Mapping: Enter a name for your mapping to help you identify it in vScope, e.g. Service Desk
- Enter Azure Object ID: Provide the object ID of the user/group in Azure. You can find the group ID in Azure.
- Preview and Add Mapping: Review your mapping settings, then click Add.
Group mapping will apply upon next user login.
Troubleshooting
Wrong username, password or authentication method. Try again or contact your administrator.
This is a generic error that can relate to anything from configuration to permissions.
-
If the user exists in vScope:
- Ensure that you have set Authentication to SSO.
-
If the user does not exists in vScope:
- Ensure that the accounts have an registered email (same as user principal name) in Microsoft Entra ID.
-
If the user does not exist in vScope
- Ensure that the user account is in the correct tenant in Microsoft Entra ID
- Ensure that the accounts have permissions to login to vScope (e.g. via Group Mapping) or that it has a registered email in Microsoft Entra ID.
Group mapping not working
Ensure that the number of groups where a user is a member, is not exceeding the limit that Microsoft Entra ID applies in its JWT. Learn more on Configure group claims for applications by using Microsoft Entra ID. To solve this, you to configure group claims for a gallery or non-gallery SAML application via single sign-on (SSO). Learn more about Adding group claims to tokens for SAML applications using SSO configuration.