Azure
The Azure Resource Manager (Azure RM) credentials includes several platforms: Azure Resources, Microsoft Entra ID, Microsoft Endpoint (Intune), Microsoft Defender. To inventory Azure Resource Manager (Azure RM), vScope needs an app registration with Graph/Defender permissions plus Reader on the subscriptions/platforms you want to scan. Here’s how its done.
Prerequisites
Section titled “Prerequisites”- Permission to create app registrations and grant admin consent in your tenant. See Azure Permissions
- Reader access (or ability to assign it) on the target subscriptions.
- Azure portal access at portal.azure.com.
Set up Azure for vScope (via portal)
Section titled “Set up Azure for vScope (via portal)”1. Create the app registration
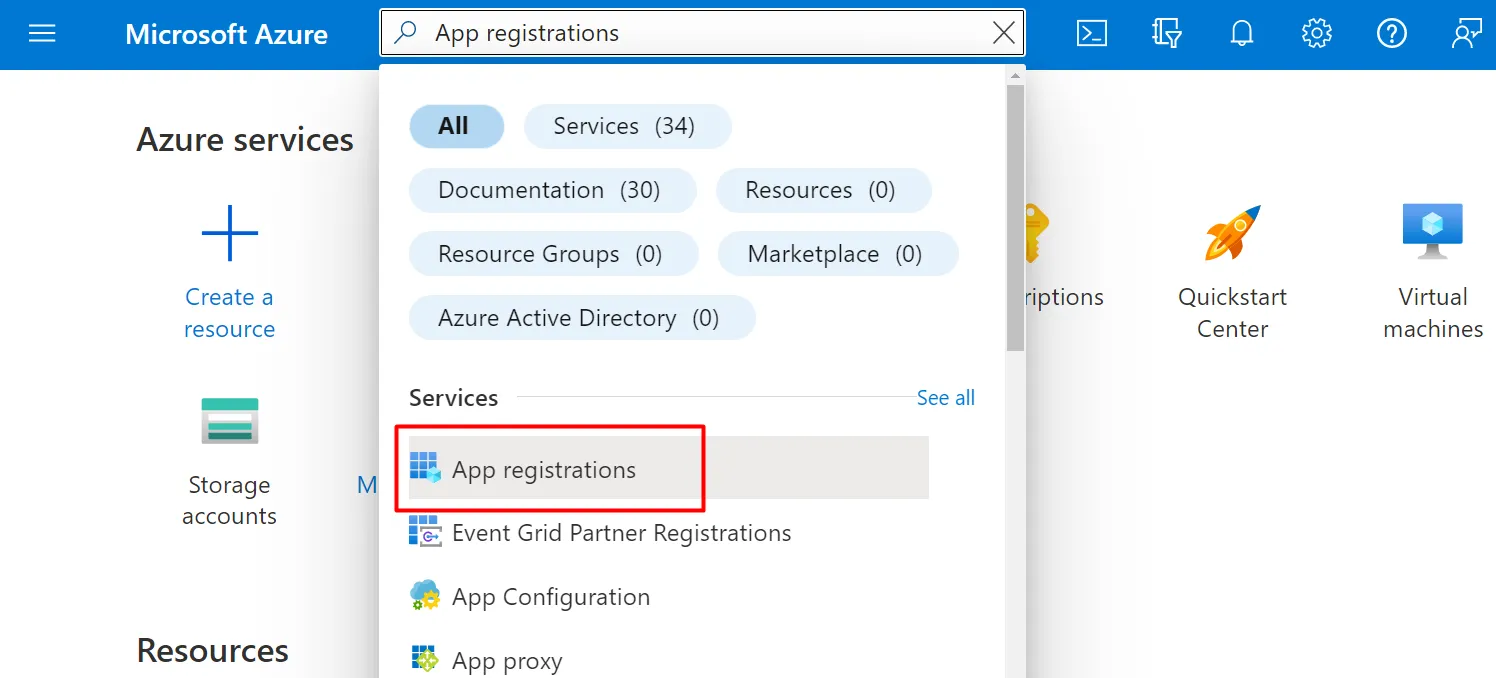
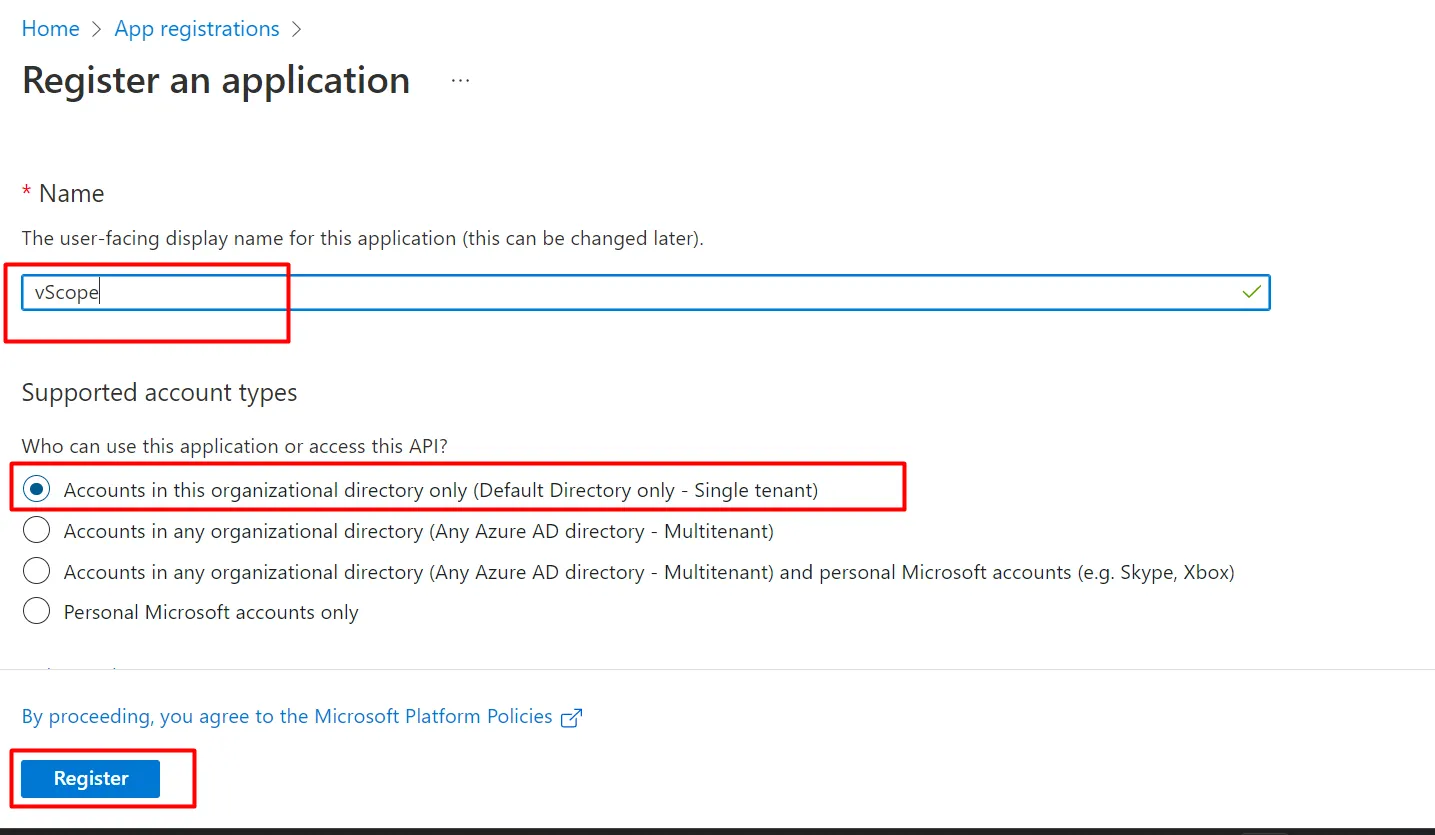
Section titled “1. Create the app registration”- In the portal, search App registrations → + New registration.
- Name it (e.g., vScope), scope to Accounts in this directory only, and click Register.
2. Add Microsoft Graph application permissions
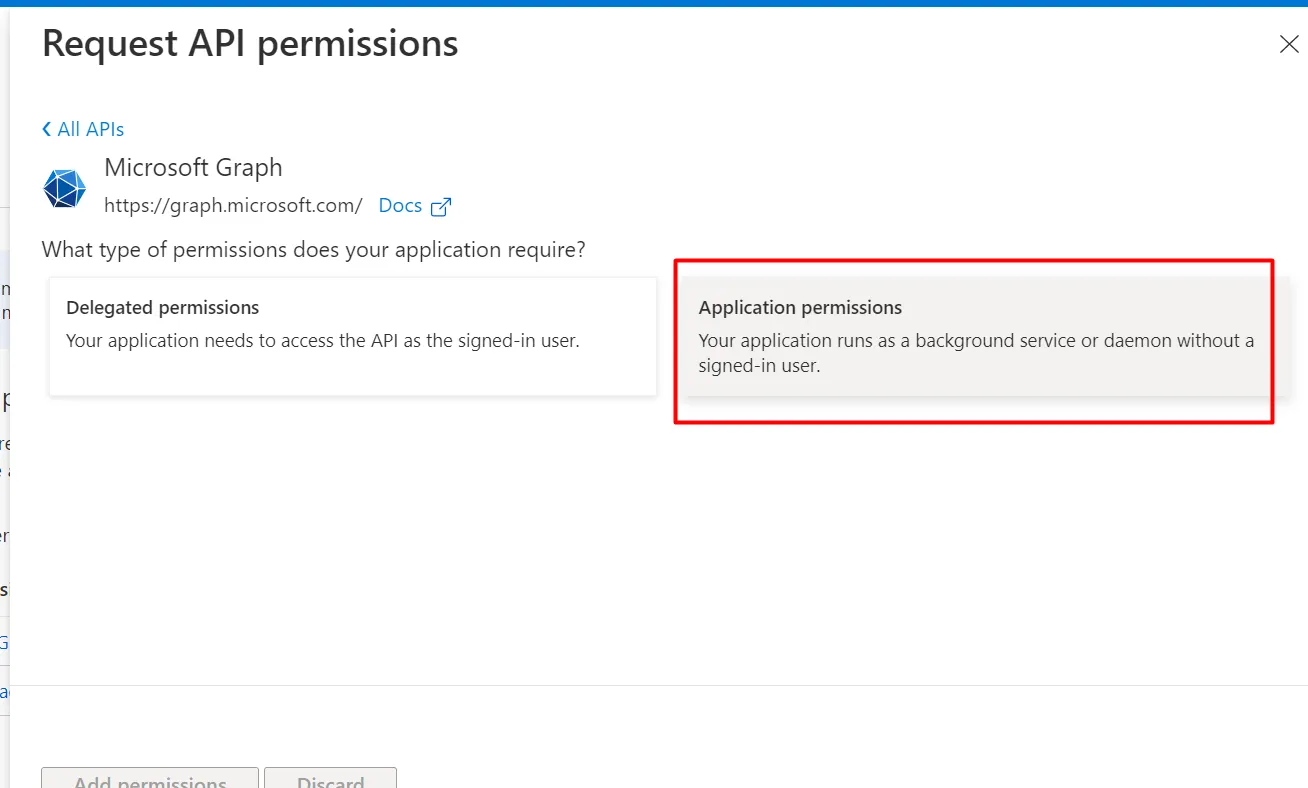
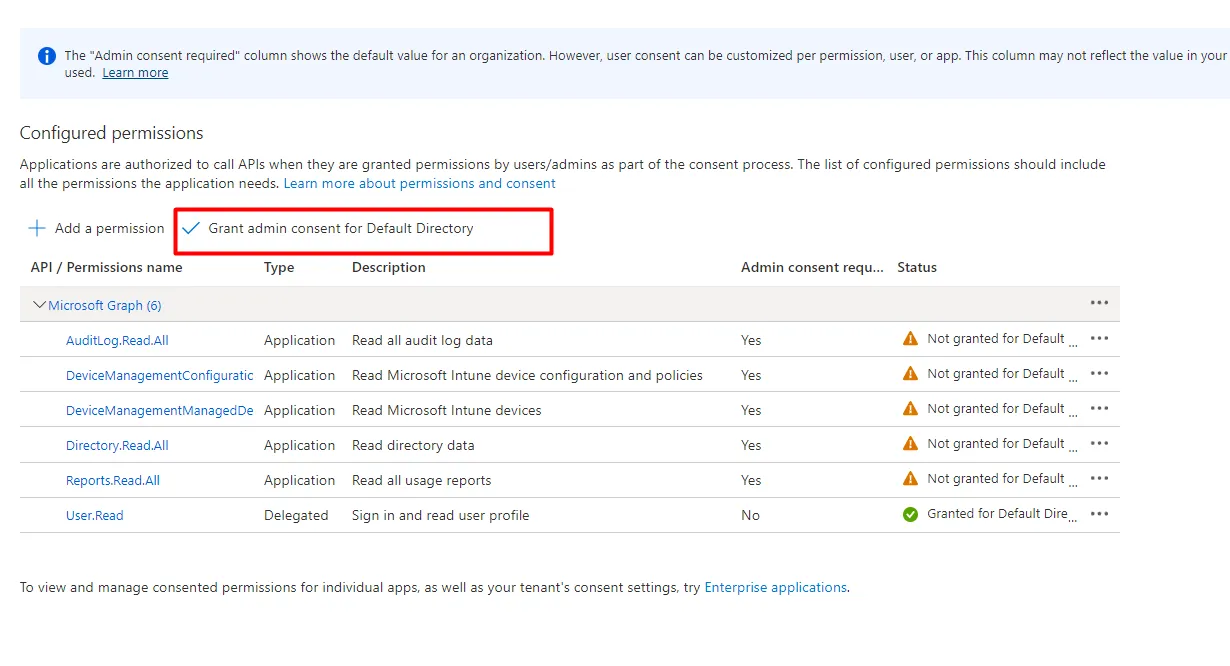
Section titled “2. Add Microsoft Graph application permissions”- Go to API permissions → + Add a permission → Microsoft Graph → Application permissions.
- Add the set of permission for your use case. Eg. Microsoft Defender, Entra ID, Endpoint Manager (Intune). See the full list at Azure permissions reference.
- Click Add permissions, then Grant admin consent.
3. Add Defender for Endpoint permissions (optional but recommended)
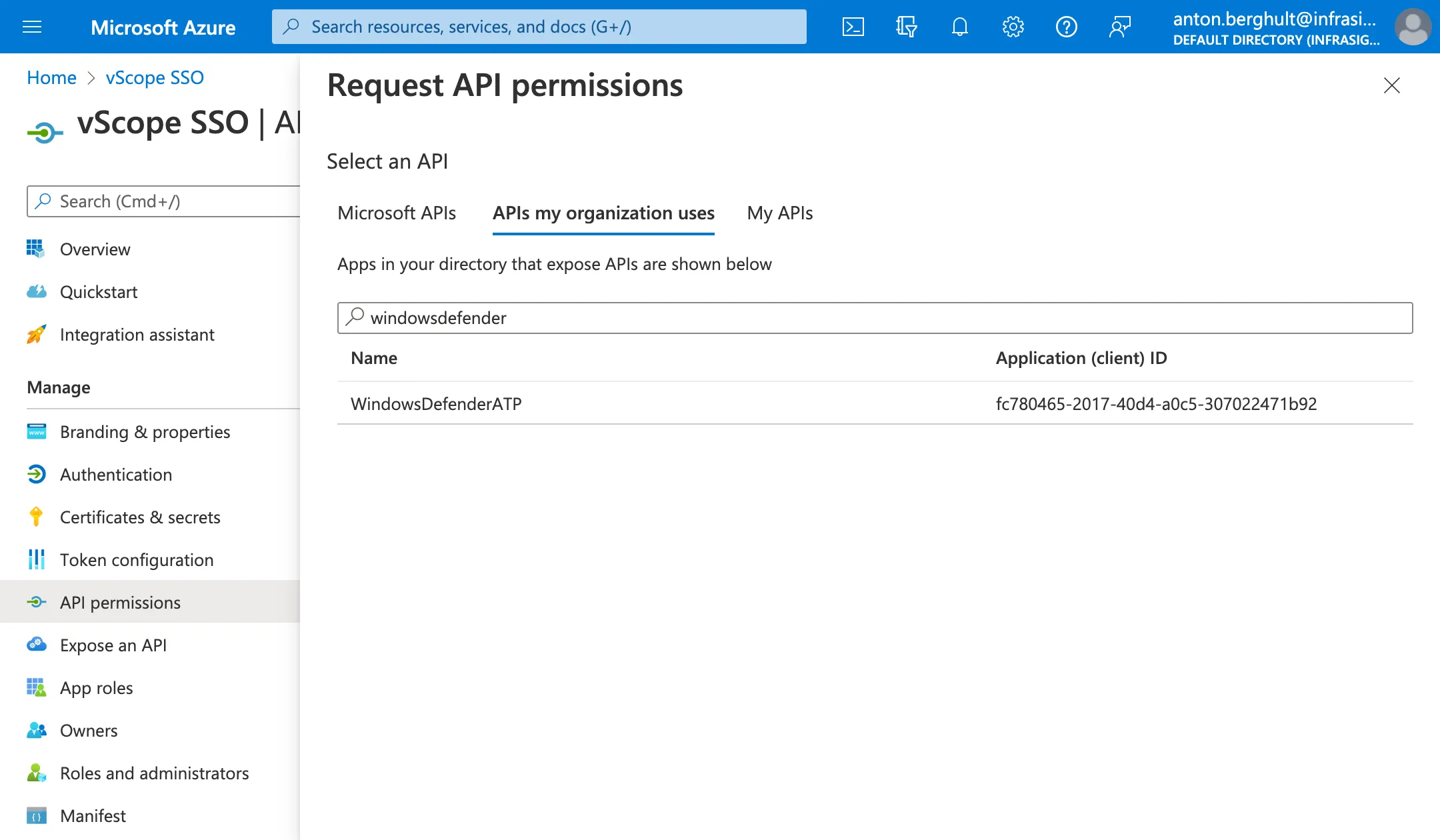
Section titled “3. Add Defender for Endpoint permissions (optional but recommended)”- + Add a permission → APIs my organization uses → search WindowsDefenderATP.
- Under Application permissions, add
AdvancedQuery.Read.AllandMachine.Read.All(see reference list). - Grant admin consent.
4. Assign Reader on the subscriptions you want inventoried
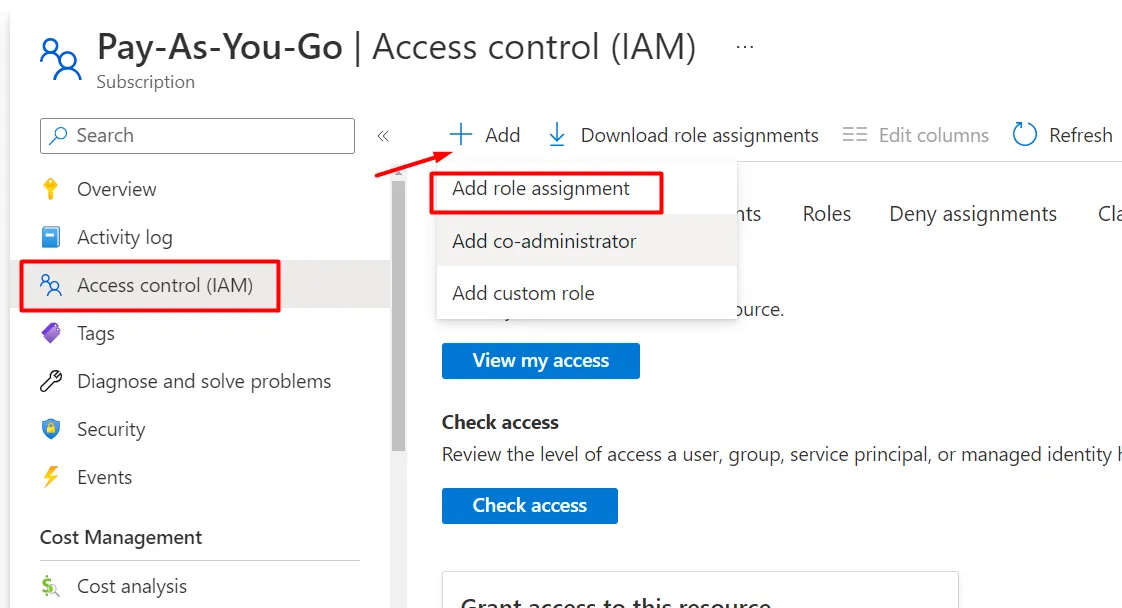
Section titled “4. Assign Reader on the subscriptions you want inventoried”- Open Subscriptions → select a subscription → Access control (IAM) → Add role assignment.
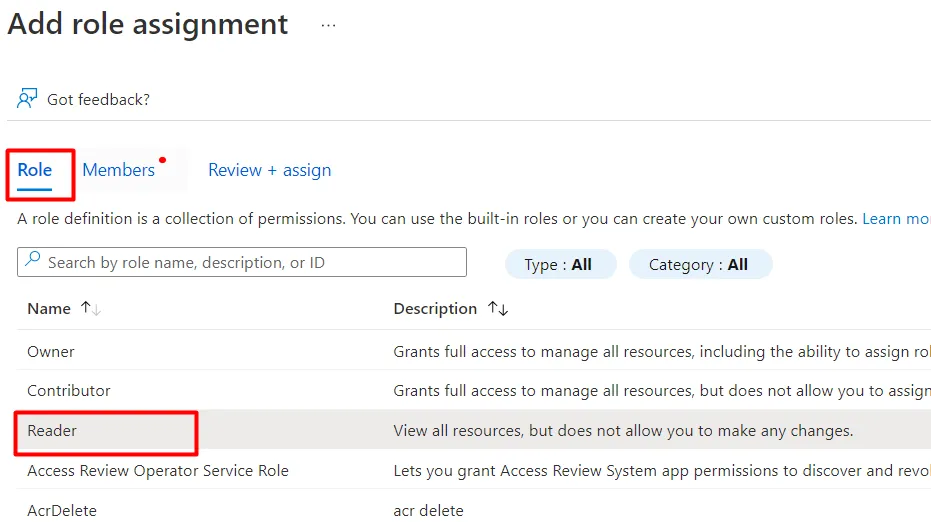
- Choose Reader → Members → select the app you just created → Review + assign.
5. Create the Azure RM credential in vScope
Section titled “5. Create the Azure RM credential in vScope”- In the app’s Overview, copy the Application (client) ID.
- In vScope: Discovery Manager → add Azure RM credential → paste the Application ID.
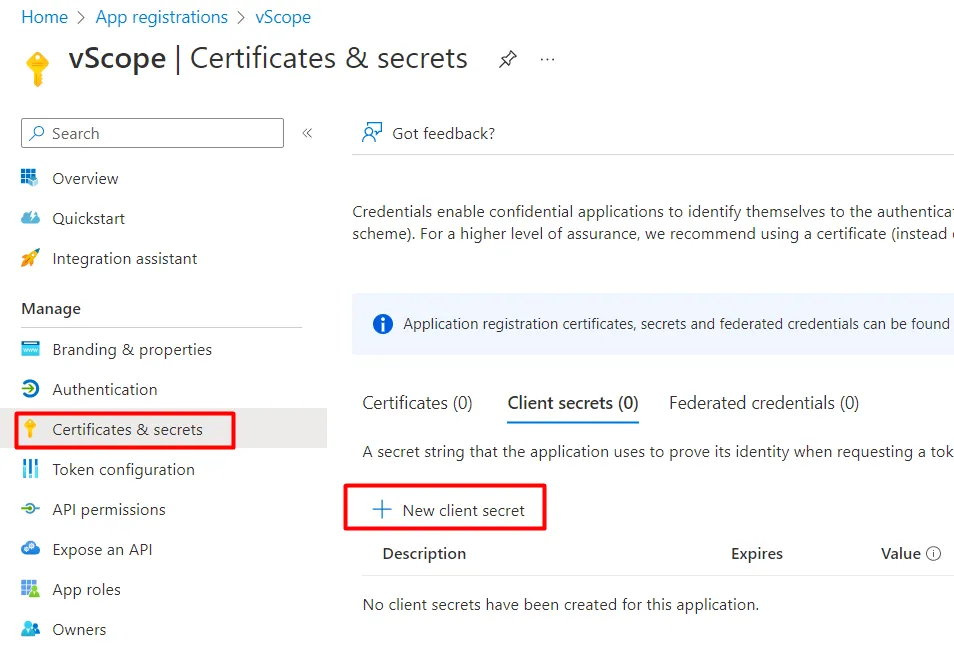
- Under Certificates & secrets, create a New client secret, copy the Value, and paste it into the credential’s Key field.
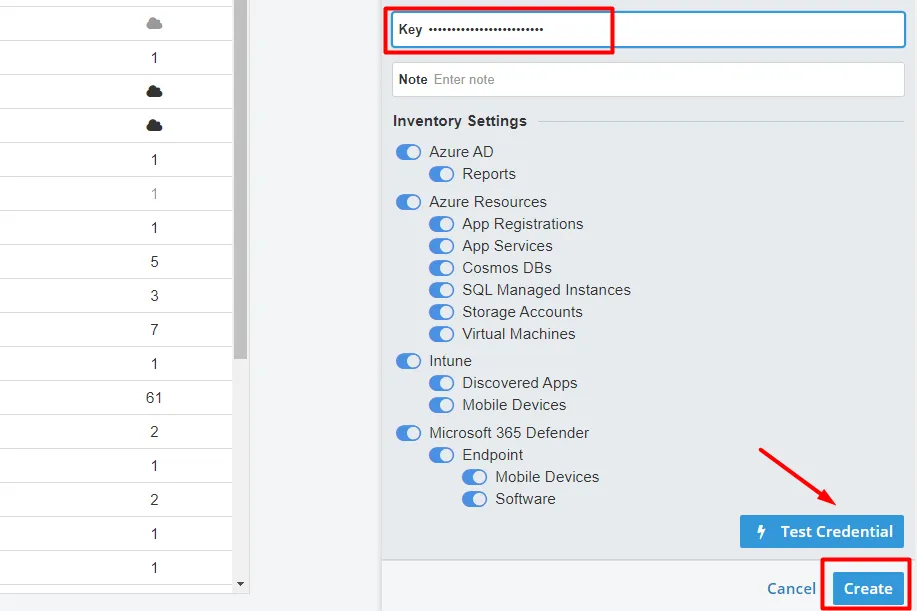
6. Verify
Section titled “6. Verify”- Click Test Credential in vScope. Green indicator = ready.
- Run a discovery; confirm Azure resources appear. If not, see Troubleshoot Azure integration.
Next steps
Section titled “Next steps”- Need to view all permission values in one place? Go to Azure permissions reference.
- Want a faster, scriptable setup? Use Automate Azure setup with PowerShell.
- Seeing duplicate devices or license name mismatches? Check Troubleshoot Azure integration.